What are SSH Keys?
SSH (Secure Shell) is a protocol that allows you to securely connect to a remote computer. One way to authenticate your connection is by using an SSH key pair, which consists of a private key and a public key.
The private key is kept on your local computer, while the public key is uploaded to the remote server. When you try to connect to the server, the server uses your public key to verify your identity. If the server determines that the keys match, it allows you to connect.
One benefit of using SSH key pairs is that it’s more secure than using a password, as the private key is much harder to crack than a password. Additionally, key pairs are more convenient, as you don’t have to remember and enter a password every time you connect to the server.
To generate an SSH key pair, you can use a command line tool such as ssh-keygen. This will create a private key and a public key, which you can then use to authenticate your connection to the remote server.
It’s important to keep your private key safe, as anyone who has access to it will be able to connect to your server. It’s a good idea to password-protect your private key and store it in a secure location on your local computer.
In summary, SSH key pairs are a secure and convenient way to authenticate your connection to a remote server. By using a key pair, you can connect to the server without having to enter a password, increasing the security and convenience of your remote connections.
How we can generate a SSH key pair in simple way?
# you can add a passphrase for more security, is up to you.
ssh-keygen
# remember public key it can be public, never the private.
ssh-copy-id -i ~/.ssh/mykey.pub user@host
# you can link the private key with the public testing the connection.
ssh -i ~/.ssh/mykey user@host
# also, you can use an ssh-agent with these commands.
eval $(ssh-agent -s)
ssh-add ~/.ssh/mykey
# now you can do ssh connection more easily and securely way.
ssh user@hostExample
- First, you can see how I test the connection to the server, and the Fedora server actually has an OpenSSH server installed with all configurations in a good way.
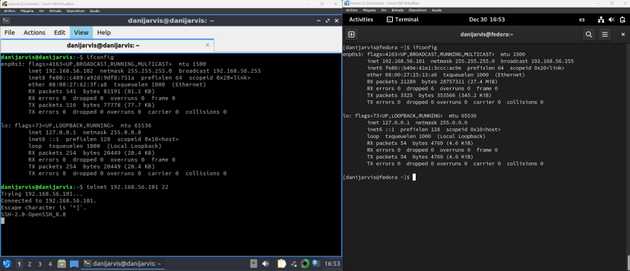
- Next on the left side, that’s actually the client running a openssh client in Lubuntu, we generated with
ssh-keygenthe ssh public and private key pairs. And you can also see it.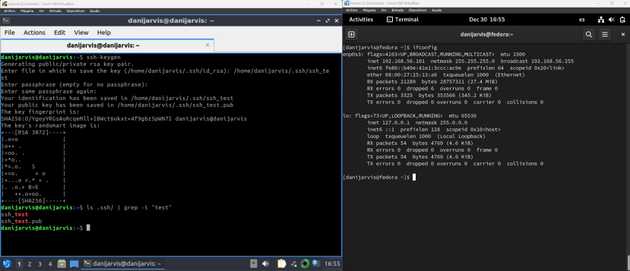
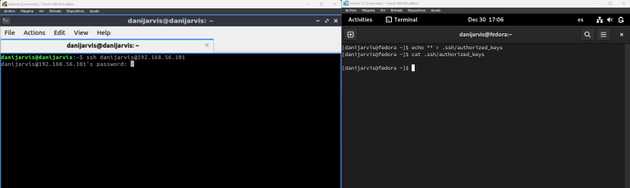
- Now, we are going to copy the public, and only the public ssh key to the remote server on Fedora on the right side using the command, in my case from my Lubuntu client left side
ssh-copy-id -i ~/.ssh/ssh_test.pub danijarvis@192.168.56.101Also you can see the authorized_keys in my Fedora server.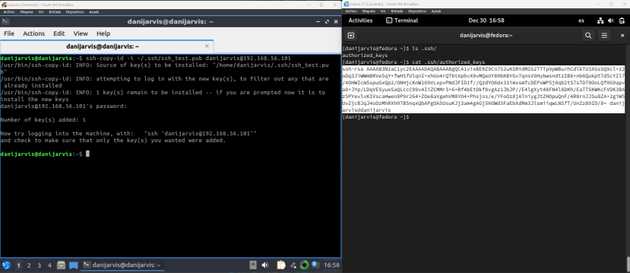
- Next, we can check the connection was already successfully done just a simple without password
ssh danijarvis@192.168.56.101, and also we can check the audit.logs as well.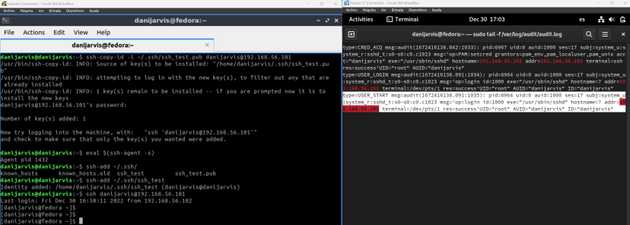
- Testing that we are actually on the same server but on different sides, from the client side and of course from the server side, but at the end is the Fedora prompt that you already see.
- Now if we want that Lubuntu to not connect anymore in the next connection, we can just remove the authorized key.
Notes
Keep in mind that I want to do this in two virtual machines, but you can do it between your host and Cloud Providers Virtual Machines, from your host and sshd containers, etc, whatever machine can run OpenSSH server on the server side and OpenSSH client in the client side. And also is very useful to use with your SCM like GitHub, bitbucket, GitLab, etc. In the way that you can use ssh for git clone, git push/pull, etc. Just remember never show the private key and everything will be fine.